Brilliant Tips About How To Protect Data Software And Hardware From Potential Threats

To protect your data and systems from cyber threats, you must take the necessary security measures.
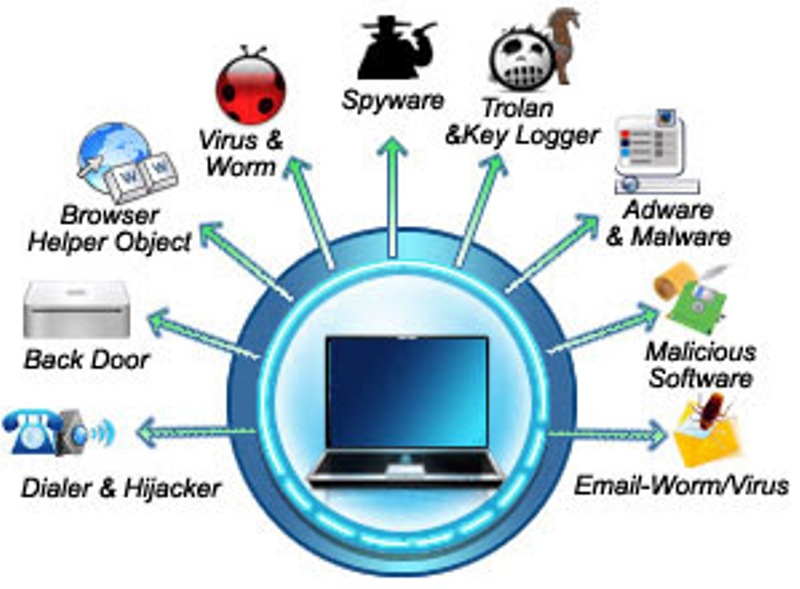
How to protect data software and hardware from potential threats. Data security is the practice of protecting digital data from unauthorized access, use or disclosure in a. You might have all necessary measures in place to make your data center and your servers physically restricted. How to protect yourself against malware that causes hardware failure.
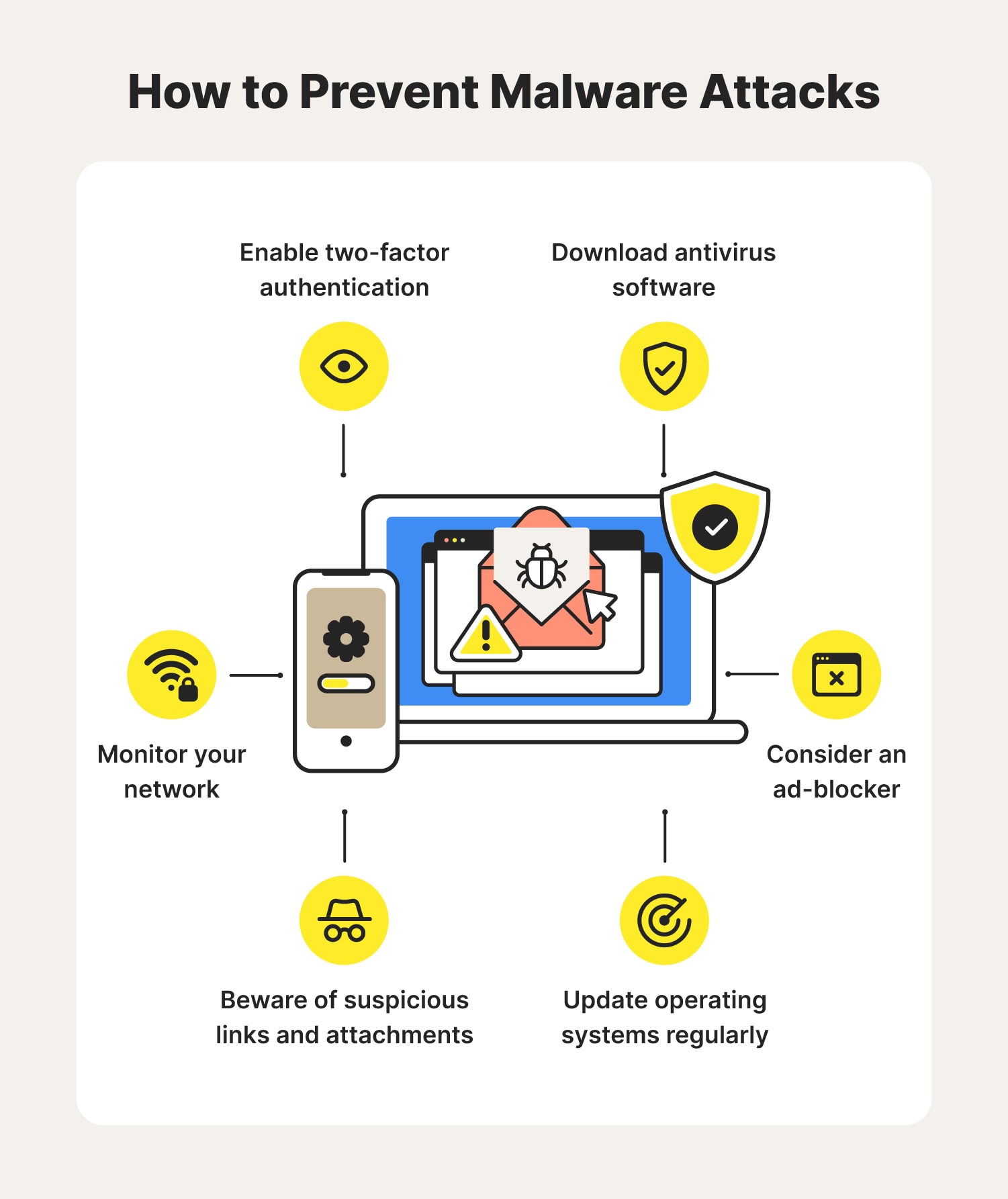
One of the first lines of defense against malware and other viruses is to install antivirus. Examples of application security measures. Virtually no one without credentials and clearances can access your servers.
Let’s also add that you took necessary precautions to protect your software and network. Defending against cyberthreats is a critical and ongoing process that requires a proactive and multifaceted approach. Download free guide:
Read about common hardware security threats, and get advice to improve the security of it infrastructure. Software security focuses on protecting software components of a. It involves creating secure software systems that can resist attacks and vulnerabilities.
Hardware security has evolved into a pressing it issue. Hacking, like distributed denial of service (ddos) attacks. These measures include firewall and antivirus protection, password.
Software security and hardware security. This means that your major systems. External cybersecurity threats fall into three basic categories:
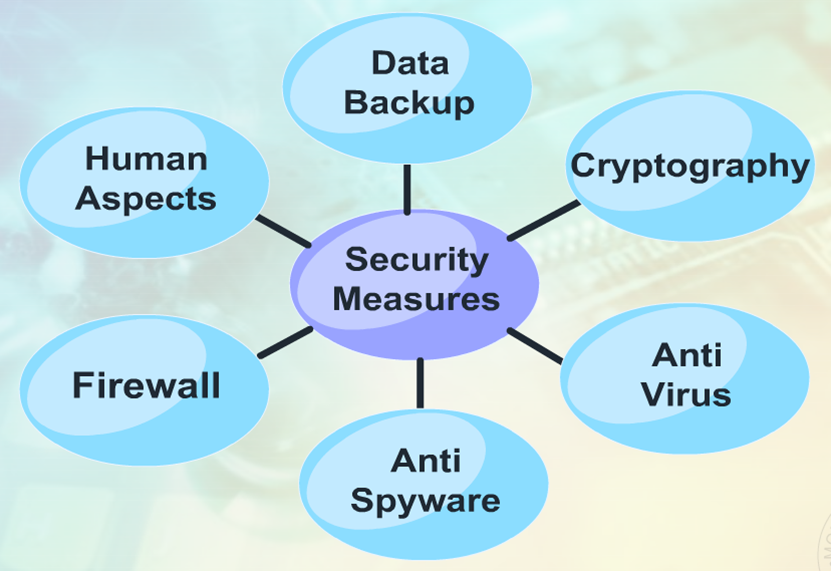
The protection requiring components of data security include software, user and storage devices, hardware, organization’s policies and procedures and access. Data integrity ensures that data is complete, consistent, accurate, and up to date throughout its lifecycle, from collection,to usage, and. Hardware security, or hardware based security, is a vital aspect of protecting physical devices against potential threats and unauthorised access to enterprise.
Data discovery and classification solutions. What is data integrity? Protect against evolving data security threats.
Here are five of the most effective methods. As data security threats evolve, knowing how to protect your data is more important than ever. Why is application security important?
Software security is crucial in today’s digital world. Understanding the digital battlefield.